Web application security evaluation combines industry-standard information security practices with tools explicitly designed to test websites, web-based services, and web applications. Web application security assessments can be carried out manually or automatically and carried out throughout the software development lifecycle (SDLC). It will typically include security measures, security audits, periodic inspections, secure coding practices, secure firewalls, vulnerability scanning, and the implementation of protocols that ensure safe operation.
In a black box penetration test, no information is provided to the tester at all. The pentester in this instance follows the approach of an unprivileged attacker, from initial access and execution through to exploitation. This scenario can be seen as the most realistic, proving how an adversary with no inside knowledge would target and compromise an organization. However, due to the extended amount of time required to research the target, black box test is one of the costly options available.
White box penetration testing involves sharing full network and system information with the tester, including network maps and credentials. A white box penetration test is useful for simulating a targeted attack on a specific system utilizing as many attack vectors as possible. Usually this type of a test is helpful at the time of product development to uncover required fixes.
Grey box tests strike a balance between depth and efficiency and can be used to simulate either an insider threat or an attack that has breached the network perimeter. In a grey box penetration test, only limited information is shared with the tester such as unprivileged login credentials and/or IP address of the target. Grey box testing is often favored by customers as the best balance between efficiency and authenticity, stripping out potentially time-consuming reconnaissance.
Know our process and Possimus delectus ex, harum, quis rerum maxime in magnam. lorem ipsum dolor sit amet, consectetur adipisicing elit.
Our Cyber Security professionals gain an understanding of the IT landscape and scope of work in an organisation during this phase. We conduct an assessment of the environment and compile data such as network architecture, application architecture, and other IT infrastructure-related data. For end-to-end testing and remediation of projects, we give a project plan with time and effort estimates. We go on to the next level after receiving approval and authorization from management.
The in-scope IT landscape is tested at this phase. We perform both manual and automated testing here.
Assess all results for severity, impact, and ease of exploitation, and assign risk ratings of High, Medium, or Low, along with explanations, proof-of-concepts, and remedial recommendations are processed in this phase. We run a revalidation test for detecting issues following the organization's remedies.
We examine and attack all of the website's operations in order to provide an accurate security image of the website, indicating which functions, webpages, or technology are vulnerable.
The primary advantage of performing a web application penetration test is that a highly qualified security specialist can attack your web application in a controlled, organised environment to detect vulnerabilities before a malicious attacker does. Attackers pose a significant threat to businesses that deploy web applications and their users; by gaining the insight provided by a penetration test, businesses may appropriately evaluate the risk to their assets and respond appropriately.
No other Pentest product combines automated scanning + expert guidance like we do.
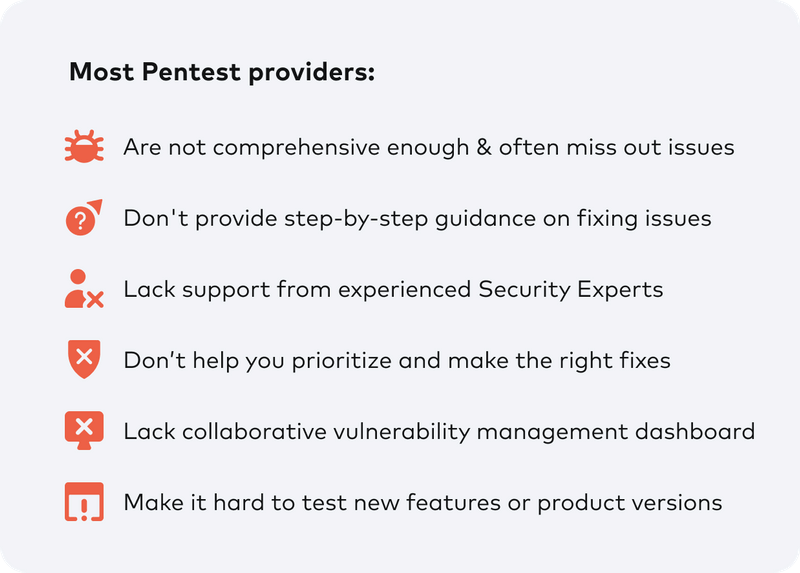
Everyone wants to make their own business the most secure and trustworthy brand for their customers.
Getting a pentest done to find and fix all the loopholes in your business is the next obvious step.
But the wrong Pentest partner could cost you months of progress and the reputation you’ve worked so hard to build.
LYFAUX Security is committed to providing businesses worldwide with cutting-edge cybersecurity solutions, and we are experts in our field. LYFAUX leverages the experience of a diverse team to provide services for a variety of technologies and complex web applications, resulting in the highest possible level of assurance.
Connect